
IoT Security Best Practices for 2025
Table of Contents
Lauch your IoT product in few weeks for MVP
Learn more
IoT Security Best Practices for 2025: Why They Matter Now
The attack surface of connected devices keeps expanding, and adversaries are adapting just as quickly. In 2025, achieving resilient IoT security is not a single feature or tool, but a disciplined program that integrates identity, encryption, visibility, and lifecycle controls end to end. This guide distills the most impactful IoT security best practices you can implement today, mapped to proven frameworks and emerging guidance for iot cyber security 2025.
What has changed in 2025:
- Devices are more capable, but also more complex, increasing the chance of exploitable misconfigurations.
- Supply chain transparency is now a board-level requirement, with SBOMs expected by regulators and customers.
- Zero Trust has become a baseline for enterprise networks, extending to operational technology (OT) and IoT fleets.
- AI is shifting to the defender’s advantage with faster anomaly detection and automated containment.
Core goals for the year:
- Treat every device as untrusted until verified.
- Encrypt everything in transit and at rest, with strong key management.
- Automate secure device provisioning, patching, monitoring, and secure decommissioning.
- Instrument your environment for early detection and rapid response.
If you are planning secure IoT app development, start by aligning architecture and backlog items with the 12 practices in this article. Where helpful, we include practical tips, architectural patterns, and links to deeper resources. For solution builders, explore platform tradeoffs and integration patterns in guides like Top 10 IoT Platforms You Should Use in 2025 (https://geekpoint.in/top-10-iot-platforms-you-should-use-in-2025) and Smart Home Automation App Development (https://geekpoint.in/smart-home-automation-app-development).
Implement Strong Device Authentication and Authorization
A secure identity foundation is essential. Without robust device and user authentication, everything else is fragile. In 2025, strong identity for IoT includes hardware roots of trust, certificate-based credentials, and policy-driven authorization.
Key actions:
- Use X.509 device certificates with mutual TLS (mTLS) wherever possible; avoid shared secrets across devices.
- Bind device identity to hardware (TPM, TEE, Secure Element) to protect private keys and enable attestation.
- Enforce least-privilege authorization through fine-grained policies for device-to-cloud and device-to-device interactions.
- Implement multi-factor authentication (MFA) for operator portals and engineering consoles.
- For application-level access, adopt OAuth 2.0/OIDC patterns with short-lived tokens and continuous session validation.
Implementation notes:
- Provision per-device unique credentials at manufacturing or first boot. Use cryptographic attestation to verify integrity.
- Rotate credentials on a schedule and on policy triggers (e.g., posture changes, tamper events).
- Gate access to message brokers and APIs with mTLS and explicit authorization lists.
Why it matters: Credential compromise remains a top initial access vector. Strong authentication and authorization are foundational iot security best practices and a prerequisite for Zero Trust.
Helpful references:
- A guide to IoT security best practices and challenges (https://iotsecurityinstitute.com/iotsec/index.php/iot-security-institute-blog/107-a-guide-to-iot-security-best-practices-and-challenges?utm_source=openai).
Adopt a Zero Trust Architecture for IoT and OT
Zero Trust principles apply directly to IoT: never trust, always verify, and assume breach. In practice, this means continuous verification of device identity, posture, and behavior before granting access to any resource.
Core Zero Trust patterns for IoT:
- Strong identity: Per-device certificates and cryptographic attestation.
- Context-aware access: Policies that consider device type, firmware version, patch level, location, and behavioral baselines.
- Micro-perimeters: Segment critical workloads and restrict east–west traffic. Make lateral movement difficult.
- Continuous monitoring: Telemetry and analytics that detect drifts and anomalies in real time.
- Just-in-time access: Temporary, least-privilege credentials for maintenance activities.
Practical steps:
- Place IoT devices behind software-defined microsegments with deny-by-default rules.
- Enforce mTLS with policy checks at gateways and brokers; evaluate device health at connection time.
- Use NAC to validate devices before they join any segment.
- Integrate your policy engine with inventory, SBOM, and vulnerability feeds.
More reading: Securing the expanding IoT with Zero Trust (https://talkingiot.io/securing-the-expanding-iot/?utm_source=openai).
Outcome: A Zero Trust approach minimizes lateral movement and reduces the blast radius if a device is compromised, a key objective for iot cyber security 2025.
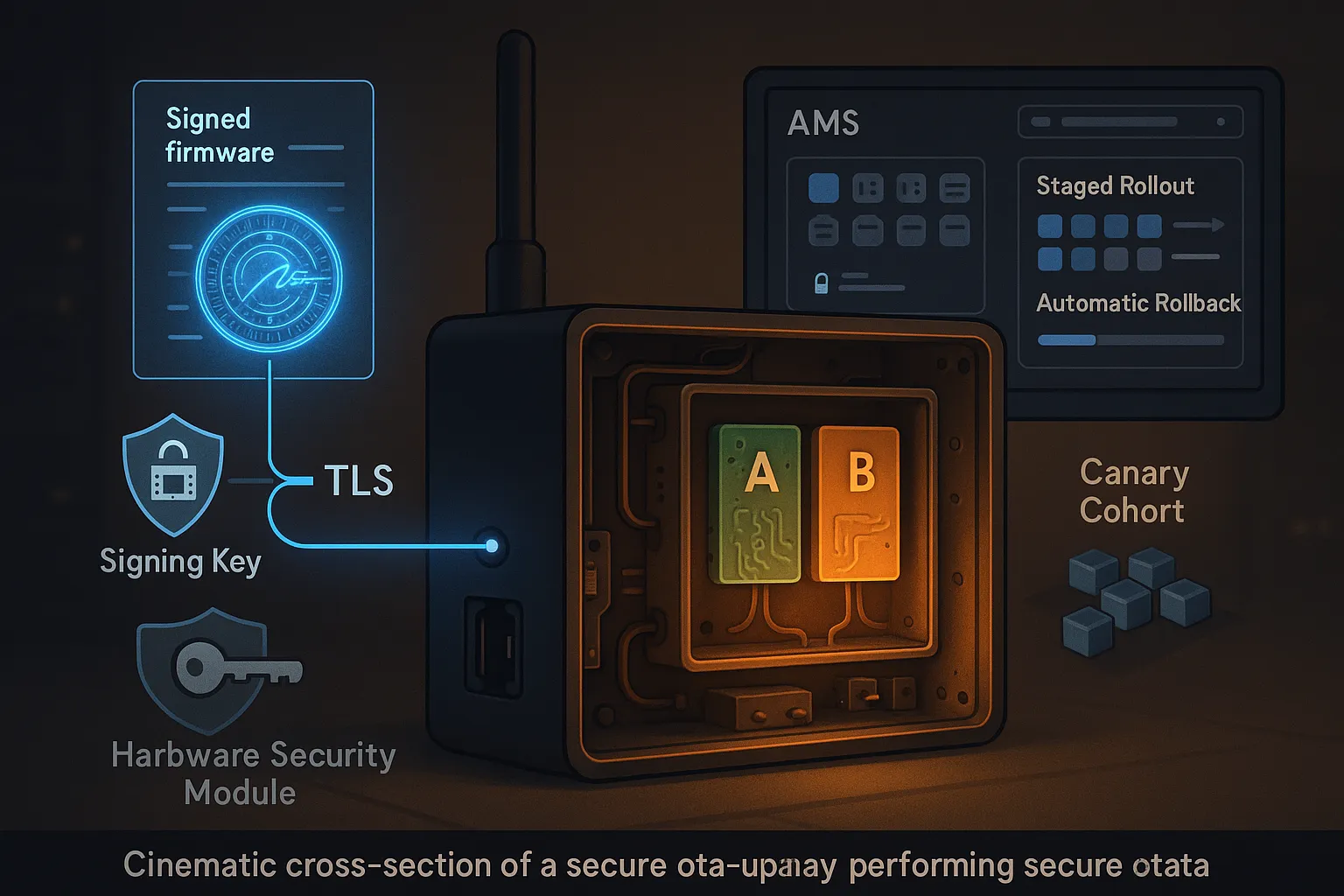
Enable Secure Over-the-Air (OTA) Updates
If you cannot patch quickly and safely, you cannot be secure. OTA is the backbone of resilience for distributed fleets, but it must be engineered to resist tampering and failure.
Security requirements for OTA:
- Signed firmware and software packages using strong algorithms (ECDSA or Ed25519) and protected signing keys (HSM-backed).
- End-to-end authenticated transport with mTLS; pin server certificates where practical.
- Version control and anti-rollback protections to prevent reintroduction of known vulnerabilities.
- Staged rollouts with percentage-based deployments, health checks, and automatic rollback on failure.
- Integrity verification on-device before installation and post-install attestation.
Operational tips:
- Separate control and data channels. Even if telemetry is delayed, ensure control plane updates can proceed securely.
- Maintain an SBOM for each build and gate deployments on vulnerability policy.
- Use delta updates and A/B partitions to minimize downtime.
- Test updates against a representative canary cohort before broad release.
Additional reading: Securing the IoT ecosystem best practices and strategies (https://www.westconcomstor.com/me/en/news/insights/2025/securing-the-iot-ecosystem-best-practices-and-strategies.html?utm_source=openai).
Result: Secure OTA updates close vulnerabilities rapidly and reliably, a cornerstone of modern iot security best practices.
Utilize Network Segmentation and Microsegmentation
Segmentation constrains an attacker’s movement and visibility. For IoT and OT, this means isolating device classes, separating critical control systems, and filtering traffic tightly.
Practical segmentation layers:
- Physical or VLAN segmentation for device categories (sensors, cameras, controllers).
- Dedicated subnets for management, OTA, telemetry, and operations.
- Firewalls and policy enforcement points at every segment boundary.
- Microsegmentation with software-defined policies that allow only specific protocols and destinations.
Implementation checklist:
- Maintain an accurate inventory and assign devices to segments based on criticality and function.
- Whitelist required protocols and ports; block broadcast and discovery across segments unless necessary.
- Monitor inter-segment traffic and enforce rate limits to deter scanning.
- Use NAC to ensure only approved devices enter appropriate VLANs.
Reference: IoT Security Institute guidance on segmentation (https://iotsecurityinstitute.com/iotsec/index.php/iot-security-institute-blog/107-a-guide-to-iot-security-best-practices-and-challenges?utm_source=openai).
Outcome: Network segmentation limits blast radius, simplifies monitoring, and strengthens compliance.
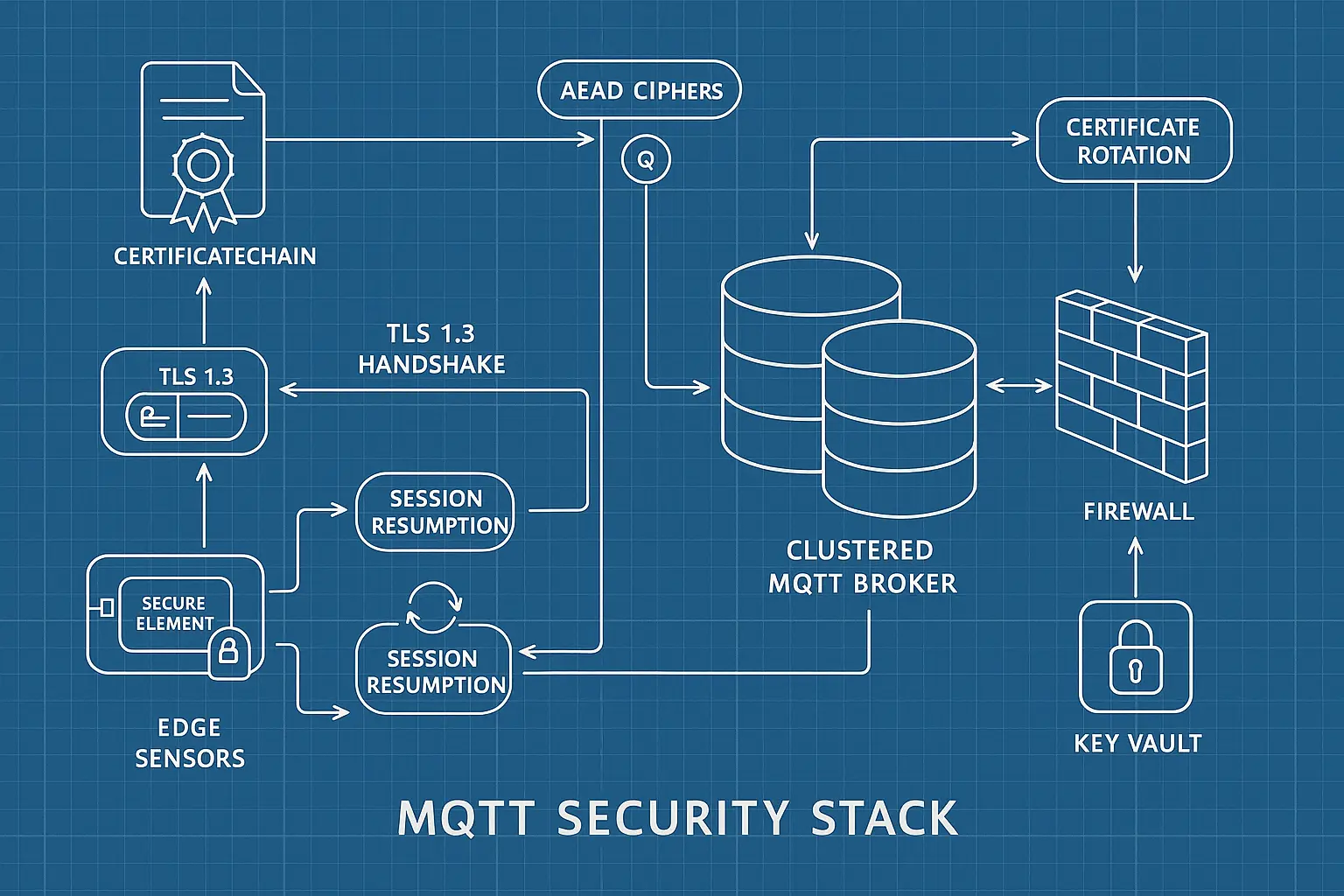
Employ Strong Encryption Protocols with MQTT TLS Encryption
Encryption must be everywhere, but especially on message buses like MQTT where devices exchange sensitive telemetry and control commands. In 2025, the minimum bar is TLS 1.3 with modern cipher suites and robust key management.
Key practices:
- Use MQTT over TLS with server authentication and, ideally, mutual TLS (mTLS) for device authentication.
- Enforce TLS 1.3; prefer AEAD ciphers such as TLS_AES_128_GCM_SHA256 or TLS_AES_256_GCM_SHA384.
- Disable legacy protocols and weak ciphers (SSLv3, TLS 1.0/1.1, RC4, 3DES).
- Use certificate pinning for brokers where operationally feasible.
- Encrypt data at rest on devices and gateways using hardware-backed keys.
MQTT TLS encryption essentials:
- Per-device client certificates signed by your PKI. Avoid shared secrets or PSKs at scale.
- Distinct broker endpoints for production vs staging; isolate and segment.
- Apply topic-level authorization; do not rely on TLS alone. A device should only publish or subscribe to scoped topics.
- Protect credentials within Secure Elements or TPMs; never store private keys in filesystem plaintext.
- Rotate certificates and keys automatically; integrate with CRL/OCSP for revocation.
Performance and reliability tips:
- Use session resumption and connection pooling where supported to reduce TLS handshake overhead.
- Compress payloads before encryption to optimize bandwidth, especially on constrained networks.
- Validate clock synchronization (secure NTP) to avoid certificate validation issues.
Further reading:
- Bryghtpath overview on IoT encryption (https://bryghtpath.com/securing-the-internet-of-things/?utm_source=openai).
For secure iot app development, build cryptography and broker policies into your acceptance criteria. Strong MQTT TLS encryption is one of the most defensible iot security best practices for both cloud and edge.
Implement AI-Driven Threat Detection and Automated Response
IoT environments generate rich telemetry. AI and machine learning can turn that telemetry into early warning signals and rapid containment.
Core capabilities:
- Behavioral baselining: Unsupervised models learn normal device patterns (frequency, byte sizes, destination sets).
- Anomaly detection: Identify deviations such as unexpected protocols, elevated error rates, or unusual topic access.
- Threat intel fusion: Correlate device behavior with known malicious IPs, certificates, or firmware indicators.
- Automated response: Quarantine devices, revoke certificates, block topics, and trigger OTA fixes via SOAR workflows.
Operational guidance:
- Stream telemetry from brokers and gateways into your SIEM; enrich with asset metadata and SBOM context.
- Keep models fresh; retrain regularly to absorb legitimate behavior changes.
- Validate alerts with canary devices to reduce false positives.
- Establish playbooks for common events (credential misuse, policy violation, suspected compromise).
Reference: Securing the expanding IoT with AI-driven defenses (https://talkingiot.io/securing-the-expanding-iot/?utm_source=openai).
Result: Faster detection, lower mean time to contain, and a feedback loop that improves policy precision over time.
Establish and Operationalize a Software Bill of Materials (SBOM)
Supply chain transparency has moved from nice-to-have to must-have. An SBOM inventories every component in your firmware and software so you can assess exposure quickly when new vulnerabilities are disclosed.
Best practices for SBOM in 2025:
- Produce SBOMs for every build using SPDX or CycloneDX. Include hashes, licenses, and dependency relationships.
- Keep SBOMs versioned and tied to device models and firmware versions.
- Automate vulnerability matching against advisories (CVE, CPE) and publish VEX status when not affected.
- Gate OTA deploys if high-severity vulnerabilities are detected in the SBOM components.
- Share SBOMs securely with customers and partners as part of your trust posture.
Tools and process:
- Integrate SBOM generation into CI/CD.
- Sign SBOM artifacts and store them alongside firmware images.
- Use policy engines to enforce minimum security bars (no known-critical vulns without mitigations).
Reference: Strategies for securing the IoT ecosystem and supply chain (https://www.westconcomstor.com/me/en/news/insights/2025/securing-the-iot-ecosystem-best-practices-and-strategies.html?utm_source=openai).
Outcome: Faster vulnerability response, improved compliance, and measurable risk reduction across your fleet.
Monitor and Manage Devices Remotely with Confidence
Proactive monitoring provides the visibility needed to detect issues early and to operate at scale. In 2025, effective remote management blends observability, configuration control, and safe remediation.
Core monitoring dimensions:
- Health and performance: CPU, memory, storage, battery, signal strength, and latency.
- Security posture: Firmware version, patch status, certificate age, policy compliance, tamper events.
- Network behavior: Connection frequency, destinations, port usage, topic access patterns.
- Operational logs: OTA success rates, error codes, and resource utilization.
Recommended practices:
- Centralize fleet inventory and tie each device to its SBOM and current configuration.
- Set SLOs for availability and security; alert on deviations.
- Use secure tunnels for remote diagnostics; log access for forensics.
- Automate remediation for common failures (re-provisioning, certificate rotation, config reset).
Build the right dashboards and data backend:
- How to Build an IoT Dashboard (https://geekpoint.in/how-to-build-an-iot-dashboard)
- Choosing the Right Database for IoT Applications (https://geekpoint.in/choosing-the-right-database-for-iot-applications)
- Industrial IoT: Building Remote Monitoring Systems (https://geekpoint.in/industrial-iot-building-remote-monitoring-systems)
Result: Higher uptime, safer operations, and quicker incident response, all aligned with iot security best practices.
Secure Device Onboarding and Decommissioning
Secure device provisioning and retirement are high-stakes moments. Weak onboarding invites impersonation; sloppy offboarding leaks secrets and data.
Secure device provisioning essentials:
- Use hardware root of trust (TPM, Secure Element) to store keys; generate keys on-device where possible.
- Just-in-time provisioning (JITP) or registration (JITR) via mTLS, validating a manufacturer-issued certificate against your PKI.
- FIDO Device Onboard (FDO) or similar protocols to bootstrap credentials without exposing secrets at rest.
- Policy-based enrollment: assign the least privilege policies, topics, and segments based on device type and function.
Decommissioning checklist:
- Rotate and revoke certificates; ensure broker and platform access is removed.
- Secure wipe of keys, credentials, and sensitive data.
- Update inventory and asset registry; archive logs for compliance.
- If devices are transferred, re-provision as new identities.
Why it matters: Secure device provisioning prevents rogue devices from joining, while strong decommissioning eliminates lingering access. Both are mandatory for secure iot app development pipelines and are critically important for iot cyber security 2025.
Reference: Unlocking the future of IoT security with secure onboarding and retirement (https://inside-association.eu/2025/01/27/unlocking-the-future-of-iot-security-challenges-trends-and-best-practices/?utm_source=openai).
Utilize Public Key Infrastructure (PKI) at Scale
PKI is the trust fabric that underpins mTLS, code signing, and secure OTA. Operating PKI at IoT scale requires thoughtful design and automation.
Design considerations:
- Hierarchy: Use an offline root CA and one or more online intermediate CAs. Separate CAs by environment or device class.
- Algorithms: Favor ECC (P-256 or Ed25519) for performance on constrained devices.
- Protocols: Use EST, CMPv2, or ACME-like flows for enrollment and renewal; avoid insecure SCEP variants.
- Revocation: Support OCSP and CRLs, with short certificate lifetimes to reduce exposure.
- Key protection: Use HSMs for CA keys and secure elements for device keys.
Operational guidance:
- Automate certificate issuance, rotation, and revocation. Integrate with your device registry.
- Monitor CA metrics and certificate expiration SLOs; alert proactively.
- Track certificate provenance and tie it to SBOMs and firmware versions.
Reference: Best practices for securing IoT communications with PKI and certificates (https://www.westconcomstor.com/me/en/news/insights/2025/securing-the-iot-ecosystem-best-practices-and-strategies.html?utm_source=openai).
Outcome: Strong, scalable authentication and integrity guarantees across devices, brokers, and services.
Keep Firmware and Software Continuously Updated
Patching is non-negotiable. Vulnerability windows are measured in days, sometimes hours. Your objective is to reduce time-to-patch while maintaining stability.
Key practices:
- Maintain a formal vulnerability management process, pulling advisories relevant to your SBOMs.
- Prioritize fixes based on exploitability and asset criticality; patch critical control systems first.
- Schedule regular update windows and support emergency out-of-band updates.
- Validate updates in pre-production environments and with canary devices.
Process accelerators:
- Integrate CVE monitoring into CI/CD; fail builds that introduce known critical vulnerabilities.
- Keep roll-back plans tested and ready.
- Capture patch status and coverage in your fleet dashboards; tie to compliance reports.
Reference: IoT Security Institute on the importance of regular updates (https://iotsecurityinstitute.com/iotsec/index.php/iot-security-institute-blog/107-a-guide-to-iot-security-best-practices-and-challenges?utm_source=openai).
Outcome: Reduced exploit window and higher fleet safety with minimal disruption.
From Strategy to Execution: A 90-Day Blueprint and Checklist
Bringing these iot security best practices to life requires a prioritized plan. Use this 90-day blueprint to make measurable progress without boiling the ocean.
Days 0–30: Establish the foundation
- Inventory devices, software versions, and SBOM coverage.
- Stand up or validate your PKI (offline root, intermediates, automated issuance).
- Enforce TLS 1.3 and mTLS on MQTT brokers; remove weak ciphers.
- Define Zero Trust segmentation policies and implement deny-by-default rules.
Days 31–60: Operationalize controls
- Implement secure OTA with signed artifacts, A/B partitions, and staged rollouts.
- Roll out device posture checks and topic-level authorization.
- Stand up AI-driven anomaly detection and SOAR playbooks for quarantine and certificate revocation.
- Implement secure device provisioning flows (JITP/JITR or FDO) and NAC-based onboarding gates.
Days 61–90: Optimize and scale
- Automate SBOM generation in CI/CD; enforce policy gates on deployments.
- Integrate vulnerability feeds and VEX into your update decisioning.
- Build dashboards for health, patch status, cert rotation, and anomaly trends.
- Conduct a purple team exercise to validate segmentation and response.
Helpful resources to accelerate delivery:
- Top 10 IoT Platforms You Should Use in 2025 (https://geekpoint.in/top-10-iot-platforms-you-should-use-in-2025)
- Choosing the Right Database for IoT Applications (https://geekpoint.in/choosing-the-right-database-for-iot-applications)
- Smart Home Automation App Development (https://geekpoint.in/smart-home-automation-app-development)
- IoT App Development Cost: Complete Guide (https://geekpoint.in/iot-app-development-cost-complete-guide)
- Industrial IoT: Building Remote Monitoring Systems (https://geekpoint.in/industrial-iot-building-remote-monitoring-systems)
- How to Build an IoT Dashboard (https://geekpoint.in/how-to-build-an-iot-dashboard)
Quick reference table:
| Practice | First step | KPI to track |
|---|---|---|
| Strong authN/Z | Issue per-device certs, enforce mTLS | % devices on mTLS, unauthorized connection attempts |
| Zero Trust | Deny-by-default segments | East–west traffic reduction, microseg policy coverage |
| Secure OTA | Sign artifacts, A/B partitions | OTA success rate, mean time to patch |
| MQTT TLS encryption | Enforce TLS 1.3 and topic ACLs | Weak cipher usage rate, cert rotation coverage |
| AI detection | Baseline traffic, enable SOAR playbooks | MTTD/MTTR, false positive rate |
| SBOM | Generate in CI/CD | % builds with SBOM, critical CVEs blocked |
| Provisioning | JITP/JITR rollout | Time to onboard, provisioning failure rate |
| PKI | Automate issuance/rotation | Expiring cert alerts resolved before expiry |
By following this blueprint and continuously refining policies, you will harden your ecosystem and support secure iot app development practices that scale with your business.
Looking for an IoT app development partner?
Are you looking for a reliable partner to help you build a stunning IoT companion app? You're in the right place.
We have 6+ years of experience building a variety of IoT apps, from healthcare to HVAC. So, if you go with us, you'll be in safe hands.
If you want to learn more, feel free to reach out and our team will be happy to set up a call to discuss your needs in more detail.
Get in touch